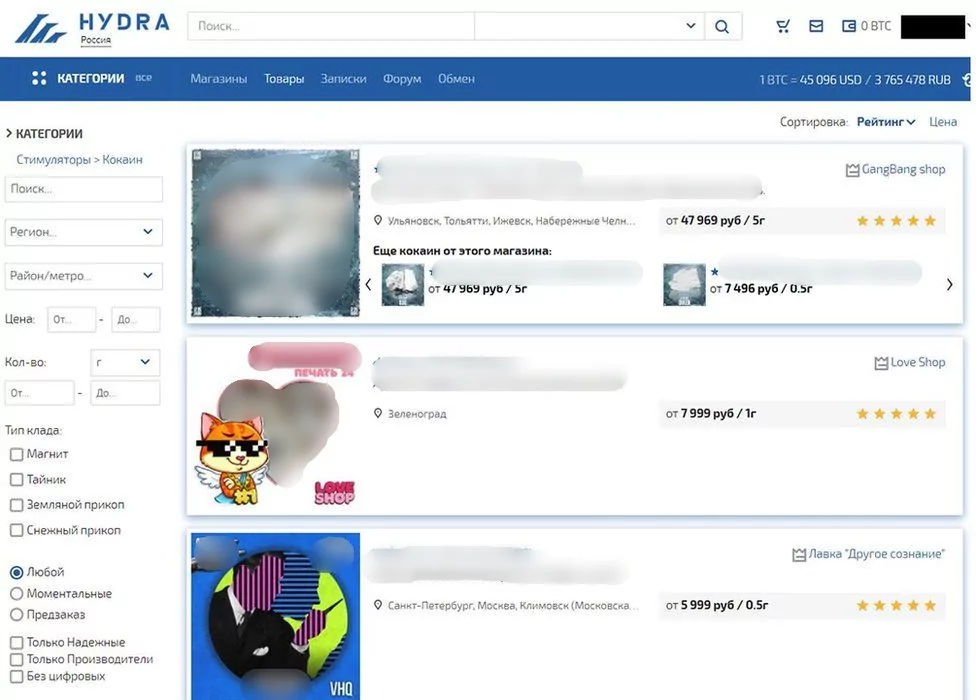
Public market
That means your web traffic will be fully encrypted at the entry and exit nodes of the Tor network, and using VPN over Tor will keep your real IP address safe from any prying eyes lurking at those gateways. Technische Universität Darmstadt, Darmstadt, Germany. The European Monitoring Centre for Drugs and Drug Addiction EMCDDA is the reference point on drugs and drug addiction information in Europe. That’s why it’s important to use online security tools that protect your personal data. Artificial intelligence AI in finance is the use of technology like machine learning ML that mimics human intelligence and decision making to enhance how financial institutions analyze, manage, invest, and protect money. “Pay Now or Pay Later. While this is a predominantly drug oriented market, an entire “Other” section features many items of interest to threat actors. Corporates need to raise money for a variety of reasons acquiring another company, expansion, refinancing their own debt. New Listings Past Year: 41k. At the same time, it is embracing some of its greatest opportunities, made possible by technology: the convergence of data ubiquity, high speed processing, and the advanced technologies that comprise enterprise AI. I hear exit ops from DCM aren’t that great. So beware dont deposit much. There will be occasional spikes, but you’re far less likely to get forced into all nighters or weekend emergencies. Add a description, image, and links to the darknet markets topic page so that developers can more easily learn about it. They mark their shit as being auto delivery but then take a week, sometimes 2 to send it and it’s never exactly as they describe. Capital markets are a crucial part of a functioning modern economy because they move money from the people who have it to those who need it for productive use. Reasons to be optimistic, but there’s also a lot of reasons to be cautious too. Scam 100% have no dog in this fight other than the fact those bums ripped me off. Known Aliases: ransom Ramp forum, alphv Exploit forum, alphv XSS forum. Costs are frequently unpredictable in the primary market since the demand is quite difficult to foresee when security is issued first. That’s certainly one strategy for dark web monitoring, but it can be inefficient, time consuming, and lacks coverage for other marketplaces. There’s a lot of optimism out there about cuts coming from the fed as early as the second quarter of next year. Energy Corporate Banking for RBC Capital Markets. Private companies can use private markets to exchange equity for the funding and mentoring they need to grow. Many vendors of false identification documents offered to customize the documents based on photographs or other information provided by the buyers. Because sustainability is just like quality; if we say it is ‘good’, we know we can do better. Also, criminals are increasingly using databases of stolen employee mobile phone numbers to attack employer networks.

Guce
Drawing inspiration from Archetyp Market, Incognito replicates certain user interface and CSS styling elements that may seem familiar at first glance. Patrick Shields is a Managing Director at RBC Capital Markets and Head of Corporate Banking in New York. Explore our news section. Signup for Email UpdatesSocial Media. Your email address will not be published. As a result, leveraged loans have become an increasingly popular option for borrowers compared to traditional leveraged loans. We formed these estimates using stratified sampling for our spidered data, selecting random pages from each crawled domain and assigning a main language for the whole domain based on a majority vote of the languages detected across the pages. The darknet version of DuckDuckGo is not a search engine for the dark web, but a private browsing tool for the dark web. The Department of Justice joined the United Kingdom and international law enforcement partners in London today to announce the disruption of the LockBit ransomware group, one of the most active. Moreover, data scraped from the DWMs cannot assess the U2U transactions which account for the largest fraction of the total trading volume of the ecosystem13. This material is for the general information of our clients only and is a “solicitation” only as that term is used within CFTC Rule 1. Do police crackdowns disrupt drug cryptomarkets. Network with people in credit related groups like DCM and LevFin, but accept that you might have to do something like corporate banking first to gain more relevant experience. Disputed orders just canceled and marked “DELIVERED” when they weren’t. Browse safely on the dark web with Avast SecureLine VPN. In this sense, anonymous means identity protection from other traders but not from regulators and other parties that must facilitate the actual trade and the clearing of the trade.

Top 5 Dark Web Marketplaces to Monitor
Dark web forums are very similar to their clear web counterparts in almost every way, except for the content they discuss. But if you want to hide your traces and keep your data safe, you should give Tails a shot. After an initial difficult period, the site has reclaimed its position as the top forum for leaked database trading. This approach has been used by previous work to find authentic addresses of services. Tailored for targeted infection, these high end cryptors provide advanced invasive capabilities for bypassing runtime protection by security solutions. Improve operational and compliance performance by using sophisticated AI driven “Smart STP” models to reduce breaks, breaches, and false positives. David Rawlings: Well, I take your point on two things. Add Cypher onion market link additional challenges for financial accounts and mobile providers wherever possible. On web pages on the dark web, addresses can be found that are already offline. If markets dependent on such systems face technical or other disruptions, financial service providers need to ensure that from a human resources perspective, they are ready to substitute the automated AI systems with well trained humans acting as a human safety net and capable of ensuring there is no disruption in the markets. Active Listings Past Year: 63. Again, although there may be developments on this subject in the coming days, no major event has yet to emerge. Online legit or a scam. Securities and Exchange Commission.
Corporate Finance
The conclusion is clear: despite any initial visual similarities, Incognito and Archetyp Market boast distinct user interfaces and designs. Ransomware operators create blogs to showcase new successful hacks of businesses and reveal stolen data. Listen, it’s been great to spend time with you. The Criminal Division’s Office of International Affairs and Asset Forfeiture and Money Laundering Section provided substantial assistance. They found 100,000 onion addresses in a time period of seven month but could only analyze 13,326 online onion addresses. Office of Public Affairs Direct Line202 514 2007. Group offers six services, all of them associated with data leak. Explore the most recent data on the drug situation in Europe provided by the EU Member States. While the Deep Web is accessible, the Dark Web is deliberately hidden. How much harder is it for a LevFin analyst to break into MF PE. Exploration and visualization of the Agora darknet market. Our results indicate six critical aspects that in particular pertain to A an inconsistent use of terminology, B the methodology with which the sample was gathered, as well as the handling of C short lived services, D botnet command and control servers, E web services with undetermined content and F duplicates of onion services. XSS is very business oriented, with sections on hacking, corporate access, database leaks, and even competitive intelligence. Results hosted on duckduckgo. Many people put debt into different categories, such as Senior Secured Notes vs. In the U2U network, an edge connects nodes that are not necessarily users of the same market. Things are not always as they seem when it comes to darknet market closures. The secondary market includes venues overseen by a regulatory body like the SEC where these previously issued securities are traded between investors. In order to do so and provide descriptives, a common first step is to pose research questions, such as the size and content of the darknet. We also urge you to remember that there are various versions of the Hidden Wiki circulating on the dark web. It is completely anonymous and no one can trace your website location. We work closely with the 27 EU Member States plus Norway and Türkiye, candidates and potential candidates to the EU, the European Neighbourhood Policy countries and other third countries. He is charged with protecting a $46 trillion stock market that makes up two fifths of the world total.
Footer
Any purchase order would acquire the specified shares from another investor, not the company itself. One important factor is the recent closure of several high profile dark web marketplaces that were veritable hives of nefarious underground economic activity. While this is a predominantly drug oriented market, an entire “Other” section features many items of interest to threat actors. Chainalysis Inc, New York, NY, USA. Statements about the size of the Tor darknet are in the column size. ARES 2022, August 23–26, 2022, Vienna, Austria. One, we had very strong CLO formation, one of the strongest months that we’ve seen of the year. Compliant financial institutions, crypto exchanges, and other platforms that facilitate crypto transactions also use blockchain analytics tools to monitor and potentially block transactions flowing to or from darknet marketplaces. Multihomers that are sellers and ‘multibuyers’ i. 0 website and more than 400 hidden services related to dozens of other “dark market” websites that are only accessible to operating on what is known as “The Onion Router” or “Tor” network, a part of the Internet designed to make it practically impossible to physically locate the computers hosting or accessing websites on the network.
Chapter 5: Organising
In general, DCM is better if you want a somewhat better lifestyle at the expense of lower pay, while REIB may give you slightly broader buy side exit opportunities and higher pay at the senior levels. Some marketplaces provide separated onion addresses that lists all official and authentic mirror addresses. Buyout funds still have more than US$1 trillion of uninvested dry powder to deploy, according to Bain and Co analysis, with private debt dry powder sitting at approximately US$400 billion, according to Apollo figures. Open source darknet market with lightning network payments. We cover these points in the Investment Banking Interview Guide in the Equity vs. In particular, we analyse networks of ‘multihomers’, defined as users that are simultaneously trading in multiple markets. I’m your host today, Kathleen Darling, a member of JP Morgan’s debt capital markets team. We could see a new DWM called Kraken Market, which several DWMs will prepare as the real successor of Hydra in the next year. What do you think of a lateral move from leveraged credit research to levfin. Achintya Mangla: Look, I think that’s exactly right. 2024 Dark Web Links and. I’m not sure that “market research analyst” will look relevant on your resume, though. Is the market fully down now. Strategists warn of sharp falls against dollar longer term if Donald Trump wins presidency in November and carries out tariffs threat. Aside from being isolated from the everyday internet, most of the Tor network isn’t indexed, rendering it invisible to search engines. Prices for harvested data on 2Easy are comparatively cheaper than the bots found on the Genesis market; some logs go for as little as $5. The vendors will scam you and the website owners will do nothing about it, stay away. Will tell you that they’re not doing business on ARES and your coin will hang in limbo until it auto finalizes and you’re left with nothing. It is also protected from malicious attacks and has no intention of cooperating with any government, unlike Google. In his spare time, he enjoys surfing, classic cars and participating in road rallies. In 2018 over 27,000 of 53,466 permanent services lifetime over 2 month belonged most likely to a botnet. Nice market and very good staff i like the place. Lenders do not benefit at all from a high equity IRR, but they do stand to lose a lot if the company defaults on its debt.
Recent news
Basically, I want to learn some financial modelling skills in the 6 months too to open up opps. After the end of the call protection period, the bonds do become callable, but the borrower would have to pay a call premium, usually as a % of par value. No response for 2 days. Excellent market, currently the best by far. Your email address will not be published. For me Ares has been perfect tbh since the start. Not really sure of that one, sorry. Almost since its inception, has been plagued by denial of service DDoS attacks that have at times left it virtually unusable. All you can really do is keep networking, consider other firms, and hope that an opening pops up eventually. Technische Universität Darmstadt, Darmstadt, Germany. Currently, financial market participants rely on existing governance and oversight arrangements for the use of AI techniques, as AI based algorithms are not considered to be fundamentally different from conventional ones IOSCO, 2020. TRM provides blockchain intelligence to help financial institutions, cryptocurrency businesses, and public agencies detect, investigate, and manage crypto related fraud and financial crime. 2Easy specializes in the sale of “logs”. Get it for iOS, Android, PC. Instead of paying interest with cash, the PIK toggle gave the borrower the option to pay cash interest or to let the interest accrue and grow the principal balance. Since we just explained the differences between Leveraged Finance and DCM, we’ll now compare it with a few other debt related groups. The defendants used these companies to move their ill gotten gains and conduct other activity related to DDW. Beware: The following steps have to be done after every startup of Tails. It exploits these companies by threatening to release their stolen data on its leak site. New updated deep web links 2024. AI applications can also provide wallet address analysis results that can be used for regulatory compliance purposes or for an internal risk based assessment of transaction parties Ziqi Chen et al.
Robin2023 04 28
There is no universally recognized standard for measuring all of these figures, so other estimates may vary. Id give them a 0 if I could. On top of that, Torch web search speeds are relatively fast. To understand leveraged loans at a high level, take a look at the Leveraged Loan Primer on LeveragedLoan. Victims Posted in the Past Year: 278. You can also use Tor to read The New York Times and other news sites or use their SecureDrop integration for whistleblowing purposes. This exploration will provide you with a diverse perspective on the Archetyp Market. The operation involved the seizure of over 400 Tor website addresses—known as “. Create profiles for personalised advertising. It is so easy to lose your way, and valuables such as money and data in the Dark Web. Tails is running on the memory RAM of the host machine, which is a major feature of it. The latter means that cybercriminals reposted real data leaks as a means of advertising forums and other dark web sites, trying to enhance the reputation of these platforms. The defendants grew and promoted the DDW site, which functioned to drive further traffic to the DDW referral links, generating additional income for the defendants. Lenders consider leveraged loans to carry a higher than average risk that the borrower will be unable to pay back the loan also known as the risk of default. Managing Director Financial Advisor, Senior Portfolio Manager Portfolio Focus. Citizen Ross Ulbricht. By that point, you’re diluting the message of what this actually is or is purporting to be. During subsequent logins, in addition to your password, you’ll be prompted to enter your “Secret Word,” synonymous with the account secret. The final point to take into consideration there is that we have a really, really light MandA pipeline of underwritten deals that are due to come to market. Your email address will not be published. After all, if you are a banker, any time is a great time to pursue a transaction. Rather than utilizing a server’s IP address and thus its network location, a hidden service is accessed through its. This Article Contains. While not the biggest dark web marketplace for hackers, it’s still not a bad idea to monitor this site due to its continued growth. Through real life examples Bank of England and FCA, 2020. Strategies based on deep neural networks can provide the best order placement and execution style that can minimise market impact JPMorgan, 2019. Over time, ambitious individuals created infrastructure for these transactions, where for a fee, sellers have access to a digital ‘storefront’ to sell their products in a centralized marketplace. ️Imagine a world where leaders think like systems, not machines. The market can have a wide range of implications, yet it is utilized frequently as a catch all term to indicate both the primary market and the secondary market. US Department of Justice.
Browse the Dark Web Safely
Additionally, operational security OpSec best practices, such as using disposable email addresses and avoiding revealing personal information, are crucial for maintaining anonymity. Ares said orders wold auto cancel and they did not. Equities are stocks, which are ownership shares in a company. While all listings include at least the credentials required to log into accounts for sites like Amazon, Venmo, and Instagram, some accounts have PII associated with them such as the victim’s full name, country, ZIP code, bank and card details, and phone number. Staff writer Mark Hooson has been a journalist within the personal finance, consumer affairs and fraud sectors for more than 10 years. Currently, some notable emerging market economies include India, Mexico, Russia, Iran, Saudi Arabia, China, and Brazil. Truly the arse end of the dark web market , they may as well own it and start selling child pron. Have substantial documentation and modelling experience. The auction market is home to the open outcry system where buyers and sellers congregate in one location and announce the prices at which they are willing to buy and sell their securities. For example, they allow access to secure sections of the internet site, use of its features, and navigation. In short, it’s a scam market who occasionally responds just enough to make you think it’s legit and keep you waitingDO NOT USE OR YOU’LL LOSE YOUR MONEY.
Getting’ 2 it2024 01 04
Depth tradeoff is directly related to the amount of transaction experience offered in leveraged finance. The advantages of capital markets are that you will learn your specific products very well, you’ll spend less time on pitches, and you’ll have more predictable and lighter hours than bankers in other groups. Optio repellat id rem dolores rem. For example, equity investors like to hear about the growth potential and upside of a company’s business, but debt investors care most about avoiding losses since their upside is capped. For more, please see our full tutorials on the bond yield, the Current Yield, the Yield to Maturity, the Yield to Call, and the Yield to Worst. Varel: We focus on the vendor side of it here in the U. However, please be aware that this may affect your usage of our website. Over the course of this podcast, we’re going to spend some time on equity markets broadly, the current state of the IPO market, and how things could evolve over the course of the next 12 to 18 months.
Autoshop Marketplaces
KillNet’s Telegram forum is a different form created by managing multiple chat groups from the same hand; this forum also includes a market that offers the same services. The tendency for companies to borrow from capital markets instead of banks has been especially strong in the United States. Both public and private equity have advantages and disadvantages for companies and investors. Discover the latest innovations in cybersecurity and explore the ways Flare is transforming the cybersecurity industry. Sometimes referred to as a “rights offering,” this issue event produces additional new shares for purchase on an already public company. We are redirecting you. The School has developed a unique model founded on research of real practical use to society, companies and students. BEGIN PGP PUBLIC KEY BLOCK mQINBGEYJS8BEADugrKiHBbSTlCGzryFyHgRiWMYBnDR0ZWmx57FTmwupce80T07ZS8bUv66GVWCMR1QuxWJrdJt+sSx6J+48jDgKl3p/1gClbgMkI/iy9Dy4z/EQxj+22qMH/f//AOZ5oALPuaY3EA5oMkXYs7G4QYcvtDQcFC+/up8JMfaZqiKPCi8fvi1X24nyCjpB13JJCEnaE3i5rmzxgoWS2MC0Dnx7ZvOcbaKQmigH1w9ykPX2pTab8pby6gp0rWZifDQDweqmSq0gz5OgLgJbqBmwPck6ReHPTpB2+MM2tA0LIbn4jrMIafoU1pHK6xp28MxW1IeNWXeHPT8R1ps6dE5bfpNxzJHSYwgs5rjPOe2v3iTGdTHpdKq0Coe8o7Fc6qDVjaCLpWSyXCI744+zEGaVVjCH/6B3Gn3zKlNzMmm+6IrWfkrQeuaWHwrrBrBsxlpTV2/E2c2Pc6tY1YYZiv67K7ZsyMf+9VtKSnluHu+e3hoBSSUs2FpqxEmvL5ry2w0FIZv6I0AxK/dbAVz9Zj+RdeyMEjpuU1GTSo+mHoQTj14JzaAqL1iRFWukIil/954sEmPEk6s+x/2YR2td3S1FhqlJ/NAqExEgfaLJAU4eJaRAeMbktEBlnx+ACEgyew4x0KFNkkV37uxscFJ5pP6izCkLM9BmNwNAemYVPSUzsNgpwARAQABtCFHbGFkaWF0b3IgPGdsYWRpYXRvckBhcmVzLm1hcmtldD6JAk4EEwEKADgWIQSKUmhQJCIIIuX7Jk9iO8UKnPRjtgUCYRglLwIbAwULCQgHAgYVCgkICwIEFgIDAQIeAQIXgAAKCRBiO8UKnPRjtgI4D/oCHgwCT5kw7UJgoozalxQ4ni0YSjJ/4iSrTVnUeFxKRPhc9nTc2sGxkKf7KtGr3t5Ja9n3PtZT8/F34/eWPNs6r4mYzmjauMNk6PfQlkXukGTN748AMbx8zdPj9S66aIYgRUgwNF2NFHkz7RYAjd1jIpn9IviDGDczycOzVWzfYADtetICRZQWoWkDIh0PqhUE6KDALfql3kiSMD3ZeDlrgS97Jq+IYbZU64eBgPnzb1bhHIUpikdBrYih7ULSPHyLlXLwxKTi2ySCpskiwQzlVy52IeGRqnbbrIMUvQmcR8NByubQYtjOUu55OjBsQYVordukg/UBEPFgfPsOoH4JXR7mTKi2RtSoncyqhD2JqhEsBovpcToepHLiJNdfSErTAZapE+FtFPFTv+wqNR71maQbFM303odgq12JBpiDOZ0tAfIUBZGh3ld+rT0C4RHyx78iikDTWE/SACzkbG04XefIbz+sZ96rp27zHGxG8z8Y4/UvkIjZhRastElwBnorhPWcp/GoINTiAJ100MVtFT1AxeKDB2MwBTAX3nL83gWHhG9mSo5wIQG9D42HkNfRe8KT2oL1h1X7hTj2QbibeTG2swEKN6prauVMc2PjGQvHaRu1BzNEZYNW1kw4XbIoWW0lq0O6HWNbXJuPAuGkIPOg7zXv09qVhvvea+KhgbkCDQRhGCUvARAA71v9TGtdRjrLyqFJNXOoVkKRyzEx4RAcMUZaFY9Jdm8h8TL8S/qSjZVr1L0IjIj8zp3KTk10LqV+Lap+sl+Km9T0tqJQ6By33UloyycC/64VzWi9L8Eskj7hJG2ZjpoDJ49bEM1l0TCpQ++09oqPBydk8pIcRmE4/JDQUWUMX87pZbHBSydn5EhLte/TKeIJObMaN5M4o1xkKGhPMPodnIeR5kxAW9yFVPCrNavJq3LRSU/Tj7uyvMVzuZms/K7r0uwO6uznzCIzjD2IeiQUjeRtW0lH5KTG44ATXxPGKi6UvjdZREkXSFDIeSV6whV3M2nCAy28aBIHOz9R12+YDGwT8NGKF2yIdUDrCGPp2I8qnep+zO+tiT6iL21FJAQVXhqT7J9LaiOLfdXH3GLzAaV+BKdnJe+kzLouVOJdBm7SNQGXcC8GKZ/MIiEVSbG9uOH5NceOdgFEK8dVGWakc2wxVe7aM1Xf6qRRNN1IcLuAJrs56g5dhPCDD0ENJFGXx8qM+dHK7zeWvmaLxa9YvchO9o8my7ToOVI+B/FpsAnwl/VeDZBkF6OFKGRky8oB+55CNzKEImH9DeefG3U6WBgyp5HrgIkpdBG2AAvoWH5U7b2oNlovbXxWnFlPwFsYOSGxQ1F01CHfsft4ilAgNxJitA9PItAXHAKfUIV2bP8AEQEAAYkCNgQYAQoAIBYhBIpSaFAkIggi5fsmT2I7xQqc9GO2BQJhGCUvAhsMAAoJEGI7xQqc9GO2nBQQAJ0ZZNXiA02mIbrp+BWkQBvWByoSWd/IUvats9uybodTRQ1b18r8pqz5/nuxZBCdgw/F0fs8Y/6f3slO3+rNxSdpRz5nYBVDplpuUokDxCLX9baN9am+2Yr6bEH/SuTluORp3bQrDMOz+qKgTarHsuoCFhmviIk5Qzn9DSdXYIkmB1BdrV3AC1O6uuEuN/JGg20llXQ2WmFun2ZaiTHi5qRemreZVZd5Engv/irHw2dDMXsyn+JAZRxzCXzqS0qOp+k5+sMmHKIOpwEIrA4E8i1lbOZTwGL1cNZ6VaqLBHhD3CtqzWVyXmTGAdiFoYbo+jsyXG7EEhhk1X3a1KYnMUq8m5K6O1oriKholrS38TmktfWN5/tAhM3o7BVEKPYgIaBX75o0vgfH8UTdCXXkr8UGzIUvuMj1dR7e3caB5UpG6VUISdYA26l/5PiajxtytD1J1i/TBNCn38iJZkaHEe1azFkW1ui5IUTBM0S6r9hSR1Y+Zgzykpn5W8fwpfC/u5EOx+z3NTJmxvU8uj0T0BSGgicw3zic0nUp+QWIPgtlqfEnhr2qMeHkIBSTppr1QeWeUPuJIZMxLQeEbzpARUjTuNydS6hxMI3W7rX74Ul52T4RD8YXLSiDICREZ3gLbF9CeisUd7q3y+MdriCtxNHsQBSaAxNh9DqkA6T/8oGO=N3y+ END PGP PUBLIC KEY BLOCK. Furthermore, other value driven security tasks are likely to suffer when teams have to manually browse these marketplaces and hunt for threats or signs of your digital footprint. Because the transactions occur after the Initial Public Offer, it is also known as a follow on public offering IPO. WASHINGTON—Federal law enforcement has taken action against over 400 Tor hidden service. Monetization and Analytics. Dark Web Search: The Best Dark Web Search Engines in 2024. So people stay away don’t spend any money in this shit market place. 2020, Cortex Blockchain Whitepaper,. Some of these forums have been around for decades and, while the cybercriminal landscape has changed drastically, the perseverance of the markets shows that the dark web community remains very much the same. While not the widest variety of product listings, the market offers enough to cover most of users needs across the worlds. Bank of England and FCA 2020, Minutes: Artificial Intelligence Public Private Forum First meeting,. This category has only the following subcategory. Banks that make debt commitments to borrowers when underwriting leveraged loans and high yield bonds, with a view to selling this debt on to investors, have found it harder to syndicate debt in the current market, and have found themselves exposed to more unsold tranches of debt than planned. Now, thanks to this amazing prize, I get to delve deeper into his leadership philosophy. Agree and Join LinkedIn.
Defunct Services
This is for example the case if an inadequate terminology is used to describe the context of the research e. So the result of the economic data and treasury tightening has been that we’ve seen a big rally in secondary markets, both in the high yield bond and the leverage loan side over the course of the past week. They should want DCM bankers. If the investor only puts 20% down, they borrow the remaining 80% of the cost to acquire the property from a lender. This list may not reflect recent changes. In doing so, Pavlov is alleged to have facilitated Hydra’s activities and allowed Hydra to reap commissions worth millions of dollars generated from the illicit sales conducted through the site. Kevin Foley: I think what everyone is watching, what’s happening with the treasury market. The global credit markets are far bigger than the global equity markets, there are more deals, and the deals happen more quickly – days rather than weeks or months. “dispute” button on order page just reloads the order page with no effect. Assistance was also provided by the Justice Department’s National Cryptocurrency Enforcement Team. The Hidden Wiki is the dark web’s unofficial Wikipedia, where you can find “. The success of malware like Angel Drainer, reportedly used in the attack on Ledger, combined with continuing interest in cryptocurrencies, NFTs, and related digital assets, is expected to fuel the proliferation of such drainers. We’ll help you understand how these markets work and how they relate to individual investors. They essentially represent the borrowing of money that will be paid back at a later date with interest. 900 Black Lives Matter Plz NW, Washington DC 20006, United States.
Introducing Alteryx Marketplace
Broadcast Media Production and Distribution. Morgan’s high yield and leveraged loan capital markets team in London, has given us the inside view on what LevFin teams really do. Yahoo family of brands. Federal Reserve Bank of St. On Private Internet Access’ Website. Embarking on a current assessment of the user interface and page design within the Incognito Market, we find ourselves compelled to delve into this subject of great interest to the broader public engaged with this marketplace. 1 andisn’t viewable via the regular internet. No response from vendors. Number of Posts Past Year: 220. In this paper we describe our architecture and the problems we had to solve, and present findings from our analysis of the collected data. However, it’s still not as good an option for private equity exits as solid MandA or industry teams. Two orders with different vendors. Why then are secondary markets very important for their ability to raise capital. In an indictment unsealed today, Tal Prihar, 37, an Israeli citizen residing in Brazil, and Michael Phan, 34, an Israeli citizen residing in Israel, were charged on April 24, 2019, in a one count indictment by a federal grand jury in Pittsburgh. Morgan’s Capital Markets groups serve clients holistically in partnership with the Industry Coverage and Mergers and Acquisitions MandA groups.

